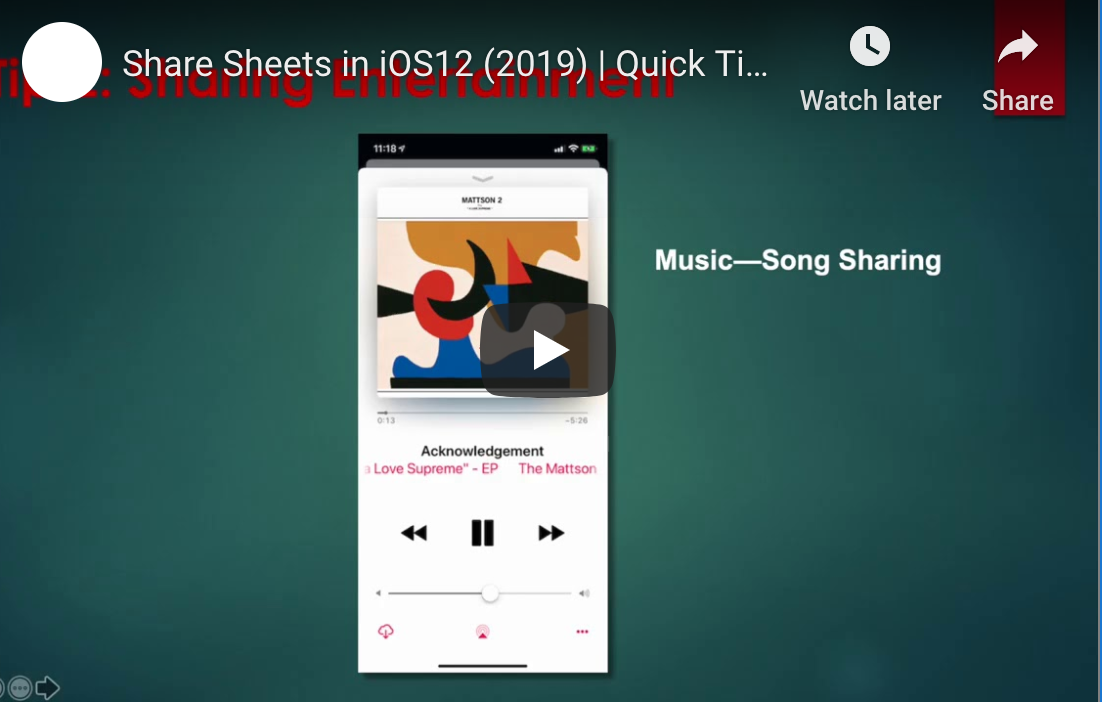
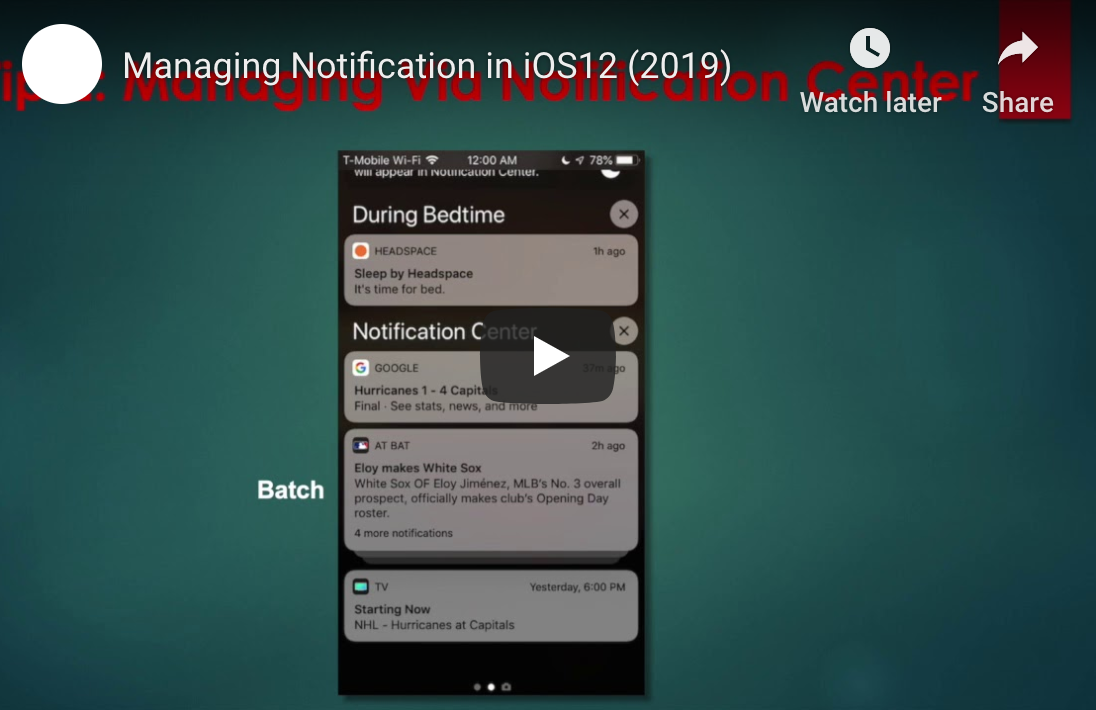
How to Use iOS12 to Instantly Share Information With Colleagues Want an easier way to communicate with your colleagues? Save time and reduce errors by learning how to instantly exchange information using iOS12’s share feature. Beginning with Apple’s release of iOS8, it has been easier to share information, files and apps with others, including […]